40 security labels are used in what type of model
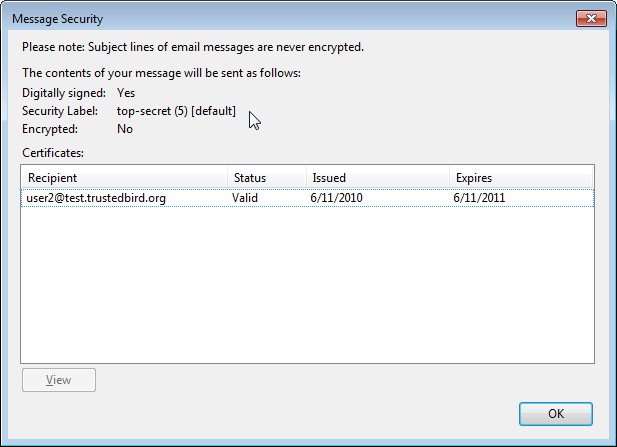
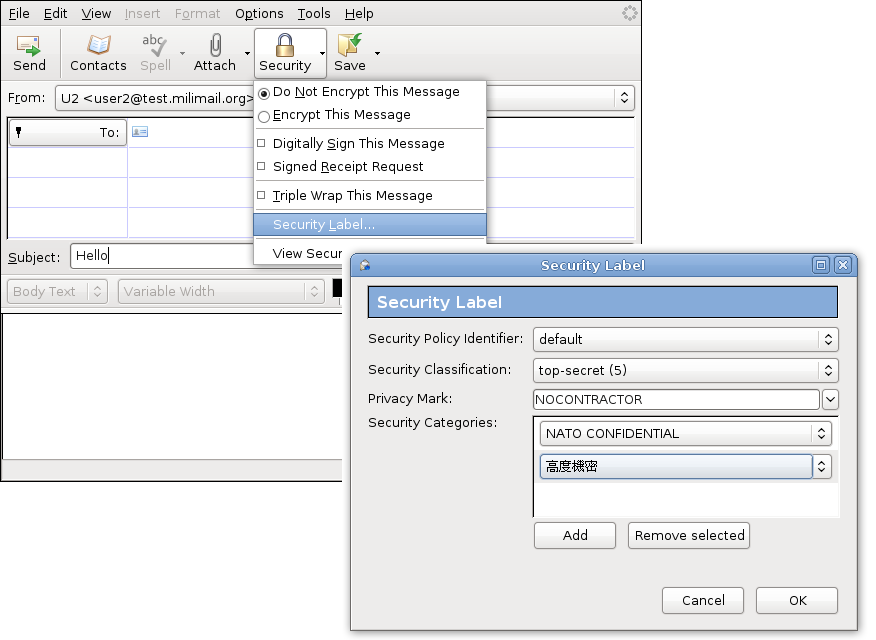
Security labels - IBM Security labels. A security label enables an installation to classify subjects andobjects according to a data classification policy, identify objectsto audit based on their classification, and protect objects such thatonly appropriately-classified subjects can access them. Objects ina multilevel-securesystem have a security label that indicates the sensitivityof the object's data. Access Control using Security Labels & Security Clearance - Isode There are two compatible specifications of Security Labels in wide use: ESS Security Labels are defined in the Internet Standard "Enhanced Security Services for S/MIME" (RFC 2634).. This specification is widely adopted, and meets all of the requirements set out above. ESS Security Labels are used in S/MIME (the Internet Standard for secure documents and email) and within STANAG 4406 (military messaging).
Chapter 3: Access Control Flashcards | Quizlet web access management. software that control what users can access when using a web browser to interact with web-based enterprise assets. markup language. a way to structure text and data sets and dictates how these will be viewed and used. Extensible Markup Language.
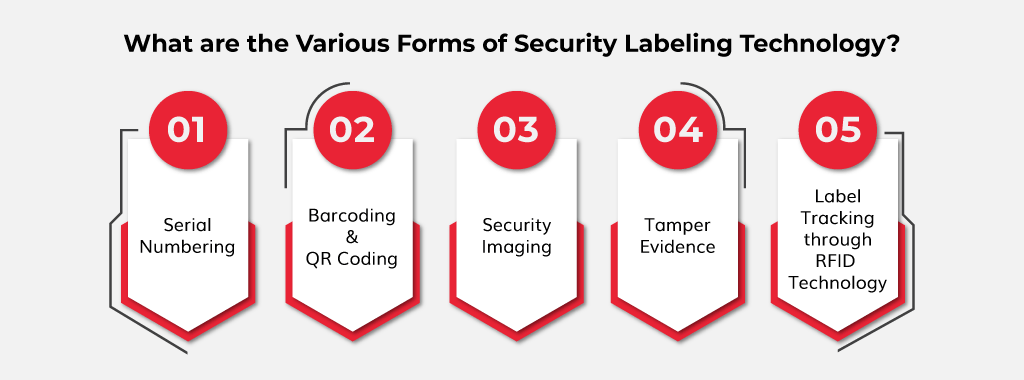
Security labels are used in what type of model
Which type of access control model assigns security level labels to ... mandatory. discretionary. attribute-based. Explanation: Mandatory access control (MAC) assigns security level labels to information and enables users with access based on their security level clearance. This is the strictest access control and is typically used in military or mission critical applications. Using Security Labels for Directory Access and Replication Control - Isode The access control model here is a very simple one: Directory Information has Security Labels; Users with appropriate Security Clearance can access this information. This overall simplicity is a key feature and benefit of this approach to access control. Where a security model is simple, there is less risk of user or administrator error. cloud.google.com › chronicle › docsUnified Data Model field list | Chronicle Security | Google Cloud 2 days ago · rule_type: string: The type of security rule. rule_author: string: Author of the security rule. rule_labels: Label: repeated: A list of rule labels that can't be captured by the other fields in security result (e.g. "reference : AnotherRule", "contributor : John"). alert_state: SecurityResult.AlertState: The alerting types of this security ...
Security labels are used in what type of model. › TR › webauthn-2Web Authentication: An API for accessing Public Key ... - W3 The client facilitates these security measures by providing the Relying Party's origin and RP ID to the authenticator for each operation. Since this is an integral part of the WebAuthn security model, user agents only expose this API to callers in secure contexts. For web contexts in particular, this only includes those accessed via a secure ... What Are Tamper-Proof Security Labels? | Tamper Proof Labels Retail. Tamper-proof security labels are used in many sectors of retail as a way to ensure that their products are safe for customers to purchase and eliminate those that are not. Retailers can also determine if a product has been used before accepting a return or exchange. Transportation. › rfc › rfc6797RFC 6797: HTTP Strict Transport Security (HSTS) - RFC Editor RFC 6797 HTTP Strict Transport Security (HSTS) November 2012 UAs typically announce to their users any issues with secure connection establishment, such as being unable to validate a TLS server certificate trust chain, or if a TLS server certificate is expired, or if a TLS host's domain name appears incorrectly in the TLS server certificate (see Section 3.1 of [RFC2818]). › TR › sparql11-querySPARQL 1.1 Query Language - W3 A blank node that is used in only one place in the query syntax can be indicated with []. A unique blank node will be used to form the triple pattern. Blank node labels are written as "_:abc" for a blank node with label "abc". The same blank node label cannot be used in two different basic graph patterns in the same query.
Security Labels - PolyLabel.com Security labels are used in an environment where you might have the necessity to identify any label tampering. There are many uses for these labels. For example, they can be used on packaging, to track data, seal freight, cargo containers, seal forensic samples, or be used in the government as a security seal. Different Types of Tamper-Proof Security Labels - MULTICOLORLABELS.COM This provides protection against false or duplicate labels, product tampering and more. Security labels are commonly used in many industries such as automobile, aerospace, marine, IT (servers, computers, modem routers, POS, etc), engineering, manufacturing, tools/devices, electronics, and construction. There are three main types of tamper-proof labels you should consider if you're a business owner of an industry mentioned above: Destructible, Checkered and Void. EOF What are Information Security Models? - Infosecacademy.io Information security models are the procedures used to validate security policies as they are projected to deliver a precise set of directions that a computer can follow to implement the vital security processes, procedures and, concepts contained in a security program. These models can be intuitive or abstractive. Security models run the directions of the road for security in operating systems. There are some security models that are most currently using for to explain the guidelines and ...
Security-labels - FHIR v4.3.0 - Health Level Seven International A security label is a concept attached to a resource or bundle that provides specific security metadata about the information it is fixed to. The Access Control decision engine uses the security label together with any provenance resources associated with the resource and other metadata (e.g. the resource type, resource contents, etc.) to. Security Labels - Hologram Dome Labels Manufacturer from Bengaluru We are offering "Hologram Security Labels" :- Security Labels are the most effective and commonly used product for Brand Authentication, and Brand Promotion. Since this holographic technology is in label form it can be used on any product or commodity. Holograms are very easy to Apply and use -Just remove and Paste. Security Labels and Stickers | Different Types | SecurityTags.com While visible plastic tags are the tool of choice for high-value items like clothing, when it comes to small items like groceries or hardware, adhesive security labels are the best option due to their affordability, disposability and simple deactivation at the point of sale. In short, labels are considered the ideal way of protecting items like books, CD's pharmaceuticals, perfumes, non-perishable groceries, hardware and more. en.wikipedia.org › wiki › Domain_Name_SystemDomain Name System - Wikipedia A domain name consists of one or more parts, technically called labels, that are conventionally concatenated, and delimited by dots, such as example.com. The right-most label conveys the top-level domain ; for example, the domain name belongs to the top-level domain com .
LBAC security label components overview - ibm.com A security label component is a database object that is part of label-based access control (LBAC). You use security label components to model your organization's security structure. A security label component can represent any criteria that you might use to decide if a user should have access to a given piece of data.
Security Seal Purpose Vinyl Destructible One-time Use Warranty Label Custom Eggshell Fragile Sticker - Buy Custom Eggshell Sticker Labels Security ...
Which of the following access control models use security labels to ... Which of the following access control models use security labels to make access decisions? Mandatory access control (MAC) Role-based access control (RBAC) Identity-based access control (IBAC) Discretionary access control (DAC) Explanation: MAC uses security labels for access decisions.
› TR › html401Forms in HTML documents - W3 The actual key sequence that causes tabbing navigation or element activation depends on the configuration of the user agent (e.g., the "tab" key is used for navigation and the "enter" key is used to activate a selected element). User agents may also define key sequences to navigate the tabbing order in reverse.
en.wikipedia.org › wiki › Information_securityInformation security - Wikipedia The type of information security classification labels selected and used will depend on the nature of the organization, with examples being: In the business sector, labels such as: Public, Sensitive, Private, Confidential.
Types of Security Labels Used in Retail Stores Placing line of sight security labels on items can also make a potential thief think twice before taking them. Security Tags. RFID Tags. Plastic security tags clip a Radio Frequency Tag directly onto an item, triggering an alarm when the chip crosses a detection sensor and alerting store employees to the theft. These tags come in a variety of forms, such as alligator, clamshell and golf ball.
Security Labels | Plain or Barcoded | SecurityTags.com Labels RF 8.2 MHz - Dummy Barcode - 1.6″x1.6″ (40x40mm) Roll of 1000. $ 28.00. View Product. Add to cart. Details.
Security Labels Market was valued US$ XX Bn in 2018 Security Labels Market by Type, Form ,Deployment Model ,Identification Method ,Composition, Application and Region is expected to reach US$ XX Bn by 2026, +91 020 6630 3320; inquiry@maximizemarketresearch.com; Toggle navigation. sales@maximizemarketresearch.com; IND +91 9607365656 ;
cloud.google.com › chronicle › docsUnified Data Model field list | Chronicle Security | Google Cloud 2 days ago · rule_type: string: The type of security rule. rule_author: string: Author of the security rule. rule_labels: Label: repeated: A list of rule labels that can't be captured by the other fields in security result (e.g. "reference : AnotherRule", "contributor : John"). alert_state: SecurityResult.AlertState: The alerting types of this security ...
Using Security Labels for Directory Access and Replication Control - Isode The access control model here is a very simple one: Directory Information has Security Labels; Users with appropriate Security Clearance can access this information. This overall simplicity is a key feature and benefit of this approach to access control. Where a security model is simple, there is less risk of user or administrator error.
Which type of access control model assigns security level labels to ... mandatory. discretionary. attribute-based. Explanation: Mandatory access control (MAC) assigns security level labels to information and enables users with access based on their security level clearance. This is the strictest access control and is typically used in military or mission critical applications.















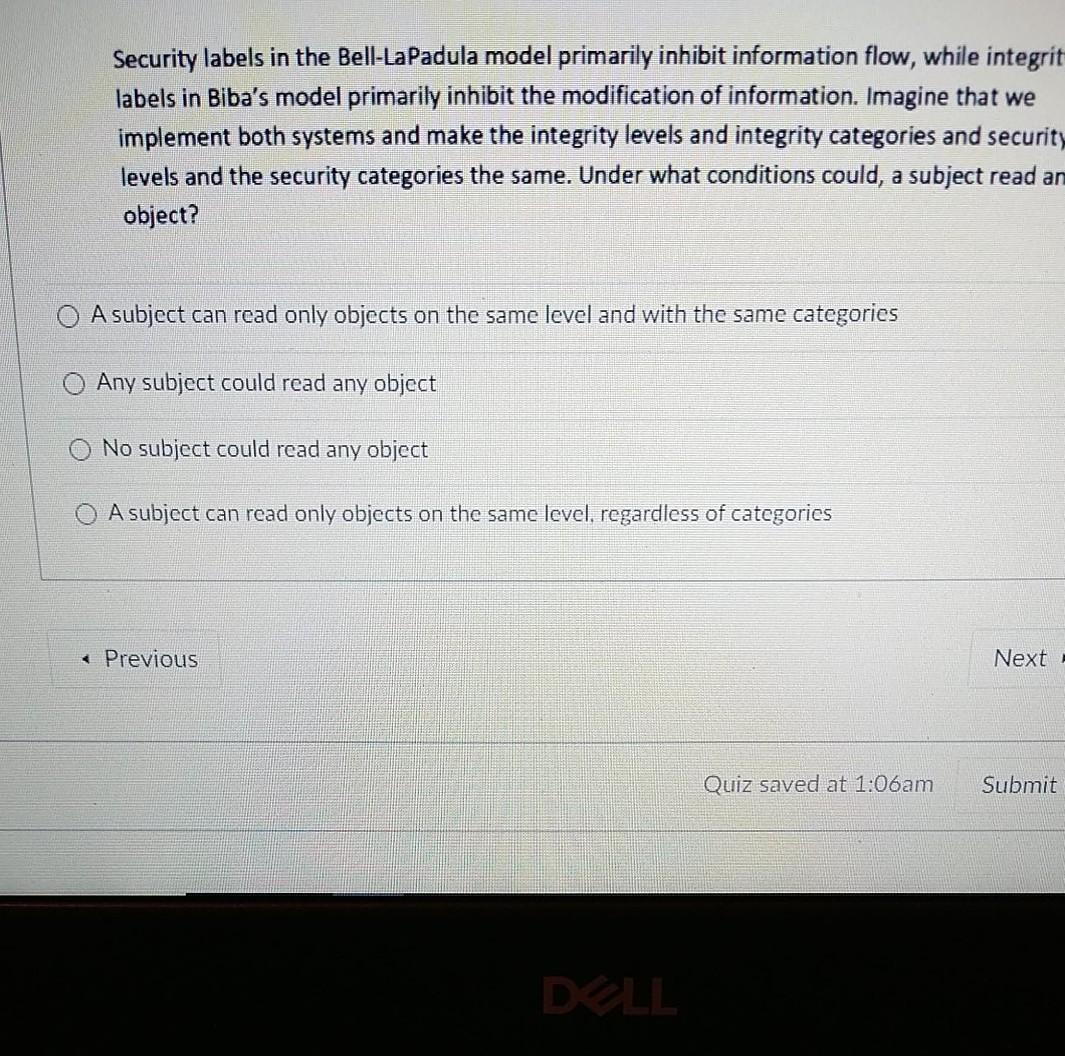



![PDF] Security model for resource availability - subject and ...](https://d3i71xaburhd42.cloudfront.net/5fa21f5740065e5adbe4ded753ed462033314858/2-Figure1-1.png)









Post a Comment for "40 security labels are used in what type of model"